Amazon S3 Block Public Access – Another Layer of Protection for Your Accounts and Buckets
Newly created Amazon S3 buckets and objects are (and always have been) private and protected by default, with the option to use Access Control Lists (ACLs) and bucket policies to grant access to other AWS accounts or to public (anonymous) requests. The ACLs and policies give you lots of flexibility. You can grant permissions to multiple accounts, restrict access to specific IP addresses, require the use of Multi-Factor Authentication (MFA), allow other accounts to upload new objects to a bucket, and much more.
We want to make sure that you use public buckets and objects as needed, while giving you tools to make sure that you don’t make them publicly accessible due to a simple mistake or misunderstanding. For example, last year we provided you with a Public indicator to let you know at a glance which buckets are publicly accessible:
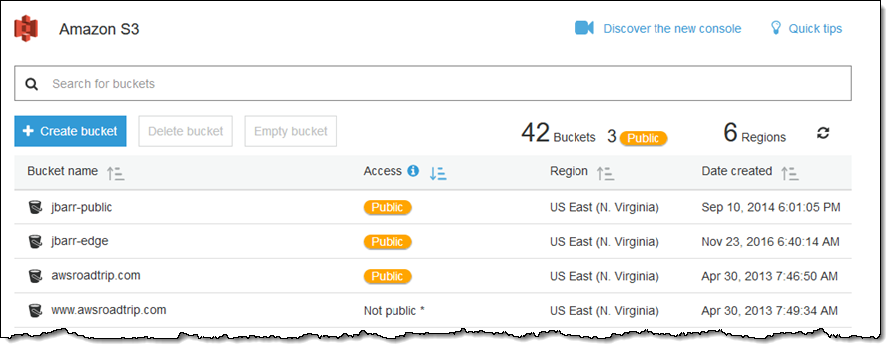
The bucket view is sorted so that public buckets appear at the top of the page by default.
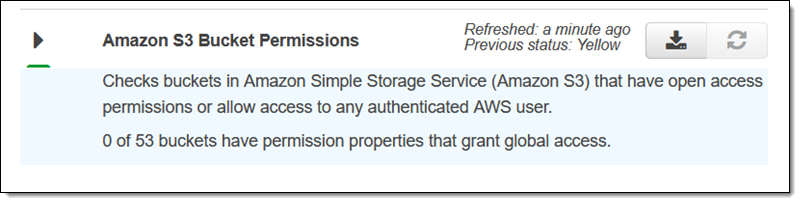
We also made Trusted Advisor‘s bucket permission check free:
New Amazon S3 Block Public Access
Today we are making it easier for you to protect your buckets and objects with the introduction of Amazon S3 Block Public Access. This is a new level of protection that works at the account level and also on individual buckets, including those that you create in the future. You have the ability to block existing public access (whether it was specified by an ACL or a policy) and to ensure that public access is not granted to newly created items. If an AWS account is used to host a data lake or another business application, blocking public access will serve as an account-level guard against accidental public exposure. Our goal is to make clear that public access is to be used for web hosting!
This feature is designed to be easy to use, and can be accessed from the S3 Console, the CLI, the S3 APIs, and from within CloudFormation templates. Let’s start with the S3 Console and a bucket that is public:
I can exercise control at the account level by clicking Public access settings for this account:
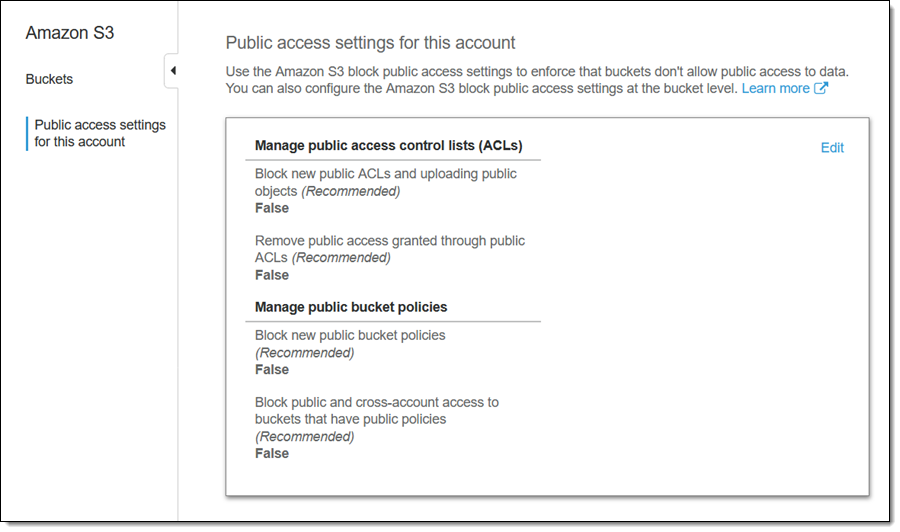
I have two options for managing public ACLs and two for managing public bucket policies. Let’s take a closer look at each one:
Block new public ACLs and uploading public objects – This option disallows the use of new public bucket or object ACLs, and is used to ensure that future PUT requests that include them will fail. It does not affect existing buckets or objects. Use this setting to protect against future attempts to use ACLs to make buckets or objects public. If an application tries to upload an object with a public ACL or if an administrator tries to apply a public access setting to the bucket, this setting will block the public access setting for the bucket or the object.
Remove public access granted through public ACLs – This option tells S3 not to evaluate any public ACL when authorizing a request, ensuring that no bucket or object can be made public by using ACLs. This setting overrides any current or future public access settings for current and future objects in the bucket. If an existing application is currently uploading objects with public ACLs to the bucket, this setting will override the setting on the object.
Block new public bucket policies – This option disallows the use of new public bucket policies, and is used to ensure that future PUT requests that include them will fail. Again, this does not affect existing buckets or objects. This setting ensures that a bucket policy cannot be updated to grant public access.
Block public and cross-account access to buckets that have public policies – If this option is set, access to buckets that are publicly accessible will be limited to the bucket owner and to AWS services. This option can be used to protect buckets that have public policies while you work to remove the policies; it serves to protect information that is logged to a bucket by an AWS service from becoming publicly accessible.
To make changes, I click Edit, check the desired public access settings, and click Save:
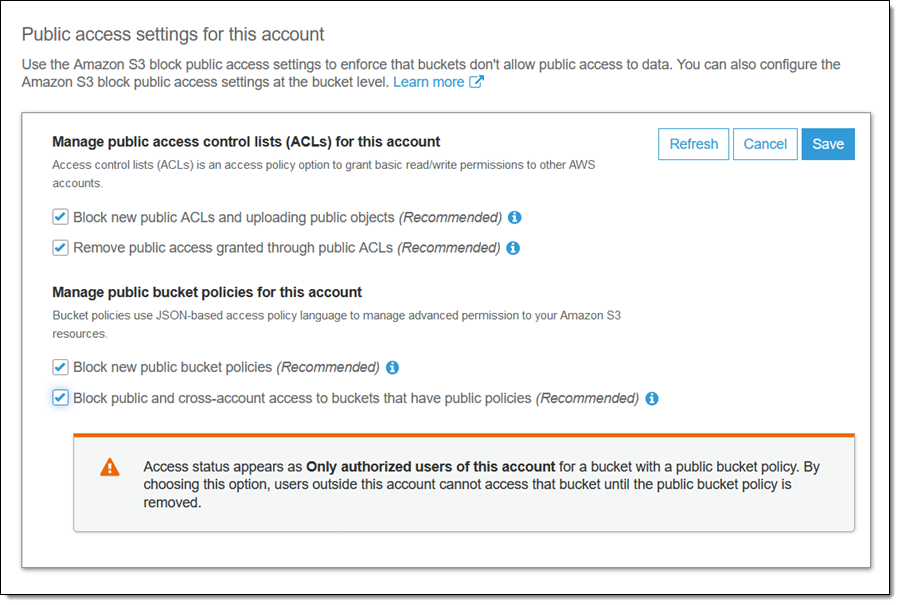
I recommend that you use these settings for any account that is used for internal AWS applications!
Then I confirm my intent:
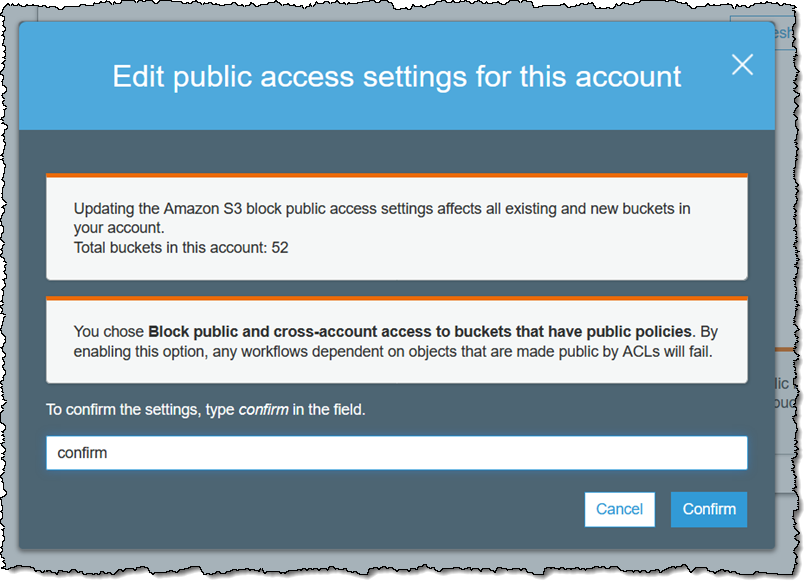
After I do this, I need to test my applications and scripts to ensure that everything still works as expected!
When I make these settings at the account level, they apply to my current buckets, and also to those that I create in the future. However, I can also set these options on individual buckets if I want to take a more fine-grained approach to access control. If I set some options at the account level and others on a bucket, the protections are additive. I select a bucket and click Edit public access settings:
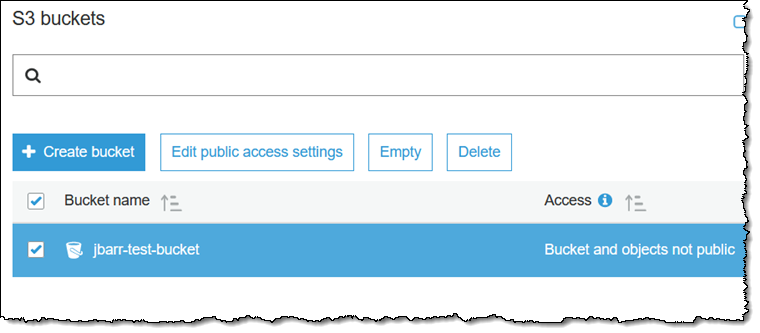
Then I select the desired options:
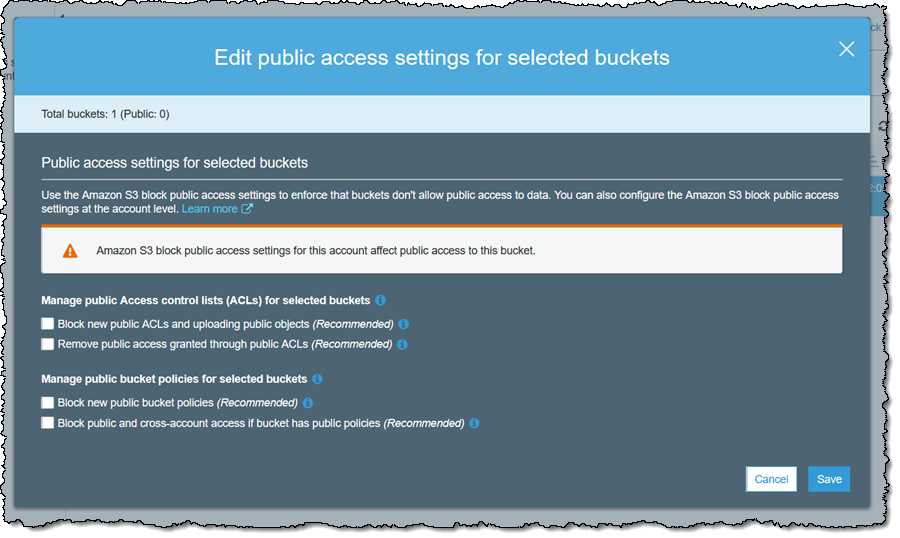
Since I have already denied all public access at the account level, this is actually redundant, but I want you to know that you have control at the bucket level. One thing to note: I cannot override an account-level setting by changing the options that I set at the bucket level.
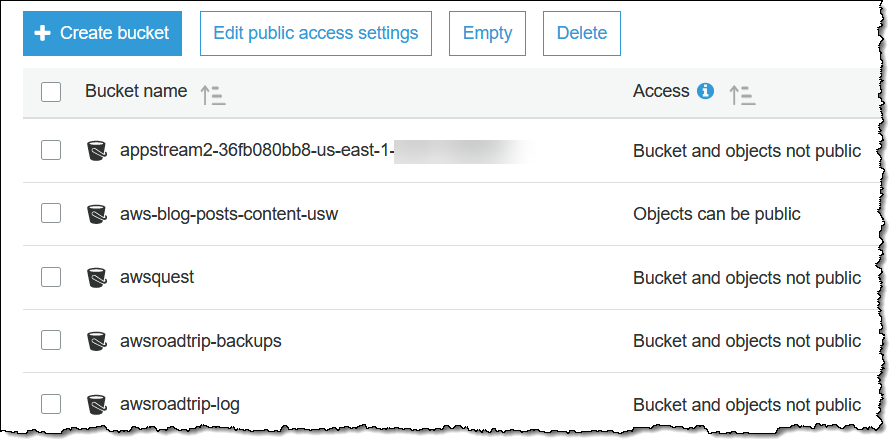
I can see the public access status of all of my buckets at a glance:
Programmatic Access
I can also access this feature by making calls to the S3 API. Here are the functions:
GetPublicAccessBlock – Retrieve the public access block options for an account or a bucket.
PutPublicAccessBlock – Set the public access block options for an account or a bucket.
DeletePublicAccessBlock – Remove the public access block options from an account or a bucket.
GetBucketPolicyStatus – See if the bucket access policy is public or not.
I can also set the options for a bucket when I create it via a CloudFormation template:
Things to Know
Here are a couple of things to keep in mind when you are making use of S3 Block Public Access:
New Buckets – Going forward, buckets that you create using the S3 Console will have all four of the settings enabled, as recommended for any application other than web hosting. You will need to disable one or more of the settings in order to make the bucket public.
Automated Reasoning – The determination of whether a given policy or ACL is considered public is made using our Zelkova Automated Reasoning system (you can read How AWS Uses Automated Reasoning to Help You Achieve Security at Scale to learn more).
Organizations – If you are using AWS Organizations, you can use a Service Control Policy (SCP) to restrict the settings that are available to the AWS account within the organization. For example, you can set the desired public access settings for any desired accounts and then use an SCP to ensure that the settings cannot be changed by the account owners.
Charges – There is no charge for the use of this feature; you pay the usual prices for all requests that you make to the S3 API.
Available Now
Amazon S3 Block Public Access is available now in all commercial AWS regions and you can (and should) start using it today!
— Jeff;
Source: AWS News


