Urgent & Important – Rotate Your Amazon RDS, Aurora, and DocumentDB Certificates
You may have already received an email or seen a console notification, but I don’t want you to be taken by surprise!
Rotate Now
If you are using Amazon Aurora, Amazon Relational Database Service (RDS), or Amazon DocumentDB and are taking advantage of SSL/TLS certificate validation when you connect to your database instances, you need to download & install a fresh certificate, rotate the certificate authority (CA) for the instances, and then reboot the instances.
If you are not using SSL/TLS connections or certificate validation, you do not need to make any updates, but I recommend that you do so in order to be ready in case you decide to use SSL/TLS connections in the future. In this case, you can use a new CLI option that rotates and stages the new certificates but avoids a restart.
The new certificate (CA-2019) is available as part of a certificate bundle that also includes the old certificate (CA-2015) so that you can make a smooth transition without getting into a chicken and egg situation.
What’s Happening?
The SSL/TLS certificates for RDS, Aurora, and DocumentDB expire and are replaced every five years as part of our standard maintenance and security discipline. Here are some important dates to know:
September 19, 2019 – The CA-2019 certificates were made available.
January 14, 2020 – Instances created on or after this date will have the new (CA-2019) certificates. You can temporarily revert to the old certificates if necessary.
February 5 to March 5, 2020 – RDS will stage (install but not activate) new certificates on existing instances. Restarting the instance will activate the certificate.
March 5, 2020 – The CA-2015 certificates will expire. Applications that use certificate validation but have not been updated will lose connectivity.
How to Rotate
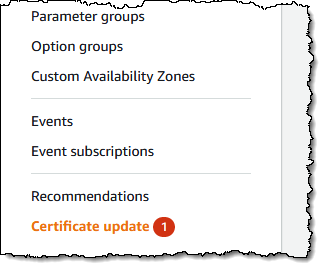
Earlier this month I created an Amazon RDS for MySQL database instance and set it aside in preparation for this blog post. As you can see from the screen shot above, the RDS console lets me know that I need to perform a Certificate update.
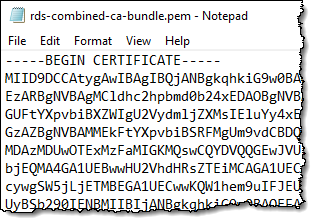
I visit Using SSL/TLS to Encrypt a Connection to a DB Instance and download a new certificate. If my database client knows how to handle certificate chains, I can download the root certificate and use it for all regions. If not, I download a certificate that is specific to the region where my database instance resides. I decide to download a bundle that contains the old and new root certificates:
Next, I update my client applications to use the new certificates. This process is specific to each app and each database client library, so I don’t have any details to share.
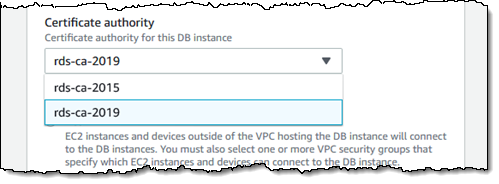
Once the client application has been updated, I change the certificate authority (CA) to rds-ca-2019. I can Modify the instance in the console, and select the new CA:
I can also do this via the CLI:
The change will take effect during the next maintenance window. I can also apply it immediately:
After my instance has been rebooted (either immediately or during the maintenance window), I test my application to ensure that it continues to work as expected.
If I am not using SSL and want to avoid a restart, I use --no-certificate-rotation-restart:
The database engine will pick up the new certificate during the next planned or unplanned restart.
I can also use the RDS ModifyDBInstance API function or a CloudFormation template to change the certificate authority.
Once again, all of this must be completed by March 5, 2020 or your applications may be unable to connect to your database instance using SSL or TLS.
Things to Know
Here are a couple of important things to know:
Amazon Aurora Serverless – AWS Certificate Manager (ACM) is used to manage certificate rotations for this database engine, and no action is necessary.
Regions – Rotation is needed for database instances in all commercial AWS regions except Asia Pacific (Hong Kong), Middle East (Bahrain), and China (Ningxia).
Cluster Scaling – If you add more nodes to an existing cluster, the new nodes will receive the CA-2019 certificate if one or more of the existing nodes already have it. Otherwise, the CA-2015 certificate will be used.
Learning More
Here are some links to additional information:
- Updating Applications to Connect to MariaDB DB Instances Using New SSL/TLS Certificates.
- Updating Applications to Connect to Microsoft SQL Server DB Instances Using New SSL/TLS Certificates.
- Updating Applications to Connect to MySQL DB Instances Using New SSL/TLS Certificates.
- Updating Applications to Connect to Oracle DB Instances Using New SSL/TLS Certificates.
- Updating Applications to Connect to PostgreSQL DB Instances Using New SSL/TLS Certificates.
- Updating Applications to Connect to Aurora MySQL DB Clusters Using New SSL/TLS Certificates.
- Updating Applications to Connect to Aurora PostgreSQL DB Clusters Using New SSL/TLS Certificates.
— Jeff;
Source: AWS News


