New – Use an AWS Transit Gateway to Simplify Your Network Architecture
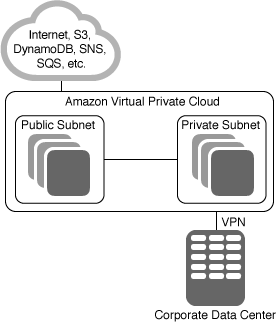 It is safe to say that Amazon Virtual Private Cloud is one of the most useful and central features of AWS. Our customers configure their VPCs in a wide variety of ways, and take advantage of numerous connectivity options and gateways including AWS Direct Connect (via Direct Connect Gateways), NAT Gateways, Internet Gateways, Egress-Only Internet Gateways, VPC Peering, AWS Managed VPN Connections, and PrivateLink.
It is safe to say that Amazon Virtual Private Cloud is one of the most useful and central features of AWS. Our customers configure their VPCs in a wide variety of ways, and take advantage of numerous connectivity options and gateways including AWS Direct Connect (via Direct Connect Gateways), NAT Gateways, Internet Gateways, Egress-Only Internet Gateways, VPC Peering, AWS Managed VPN Connections, and PrivateLink.
Because our customers benefit from the isolation and access control that they can achieve using VPCs, subnets, route tables, security groups, and network ACLs, they create a lot of them. It is not uncommon to find customers with hundreds of VPCs distributed across AWS accounts and regions in order to serve multiple lines of business, teams, projects, and so forth.
Things get a bit more complex when our customers start to set up connectivity between their VPCs. All of the connectivity options that I listed above are strictly point-to-point, so the number of VPC-to-VPC connections grows quickly.
New AWS Transit Gateway
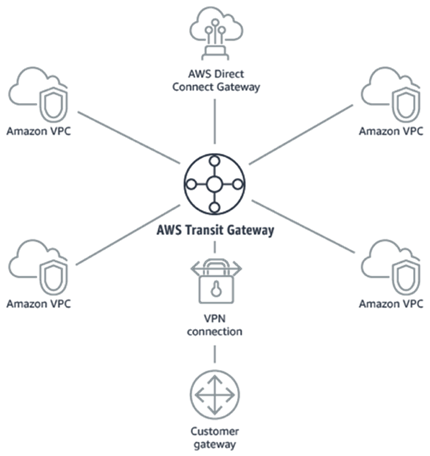
 Today we are giving you the ability to use the new AWS Transit Gateway to build a hub-and-spoke network topology. You can connect your existing VPCs, data centers, remote offices, and remote gateways to a managed Transit Gateway, with full control over network routing and security, even if your VPCs, Active Directories, shared services, and other resources span multiple AWS accounts. You can simplify your overall network architecture, reduce operational overhead, and gain the ability to centrally manage crucial aspects of your external connectivity, including security. Last but not least, you can use Transit Gateways to consolidate your existing edge connectivity and route it through a single ingress/egress point.
Today we are giving you the ability to use the new AWS Transit Gateway to build a hub-and-spoke network topology. You can connect your existing VPCs, data centers, remote offices, and remote gateways to a managed Transit Gateway, with full control over network routing and security, even if your VPCs, Active Directories, shared services, and other resources span multiple AWS accounts. You can simplify your overall network architecture, reduce operational overhead, and gain the ability to centrally manage crucial aspects of your external connectivity, including security. Last but not least, you can use Transit Gateways to consolidate your existing edge connectivity and route it through a single ingress/egress point.
Transit Gateways are easy to set up and to use, and are designed to be highly scalable and resilient. You can attach up to 5000 VPCs to each gateway and each attachment can handle up to 50 Gbits/second of bursty traffic. You can attach your AWS VPN connections to a Transit Gateway today, with Direct Connect planned for early 2019.
Creating a Transit Gateway
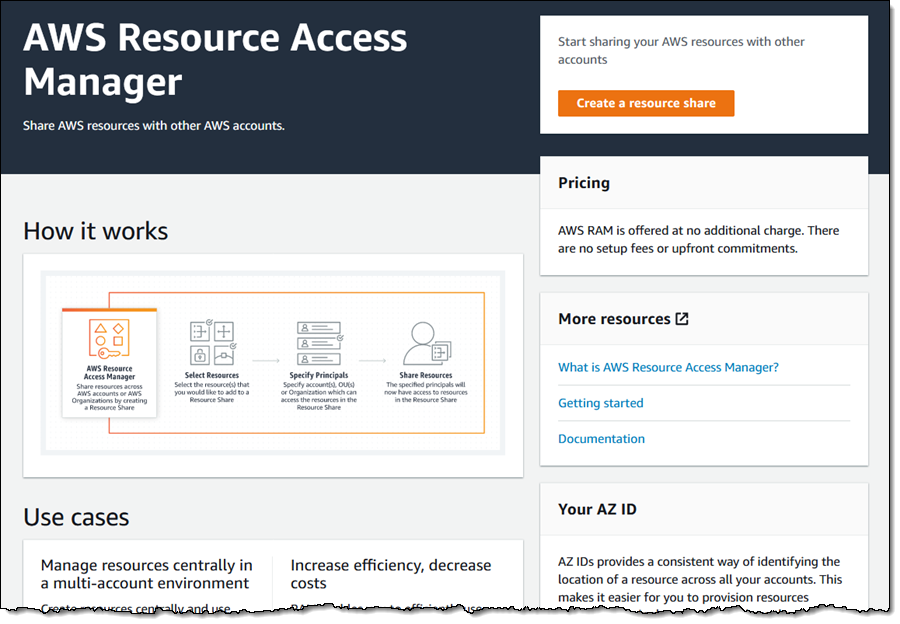
This new feature makes use of the new AWS Resource Manager, a new AWS service that makes it really easy for you to share AWS resources across accounts. An account that owns a resource simply creates a Resource Share and specifies a list of other AWS accounts that can access the resource. Transit Gateways are one of the first resource types that you can share in this fashion, with many others on the roadmap. I’ll have a lot more to say about this in the future; for now think of it as separating the concepts of ownership and access for a given AWS resource.
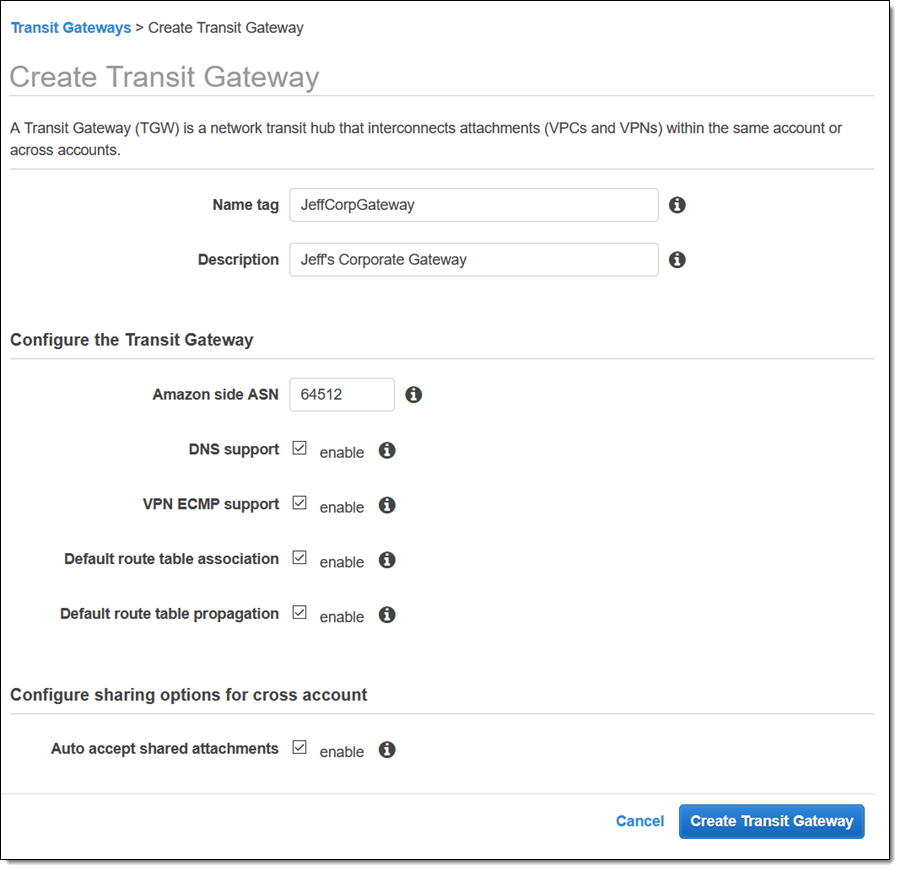
The first step is to create a Transit Gateway in my AWS account. I open up the VPC Console (CLI, API, and CloudFormation support is also available), select Transit Gateways and click Create Transit Gateway to get started. I enter a name and a description, an ASN for the Amazon side of the gateway, and can choose to automatically accept sharing requests from other accounts:
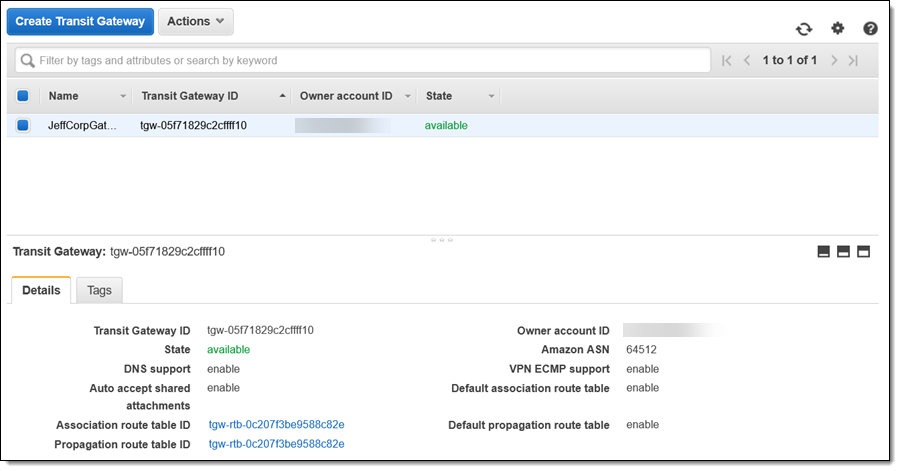
My gateway is available within minutes:
Now I can attach it to a VPC and select the subnet where I have workloads (at most one subnet per AZ):
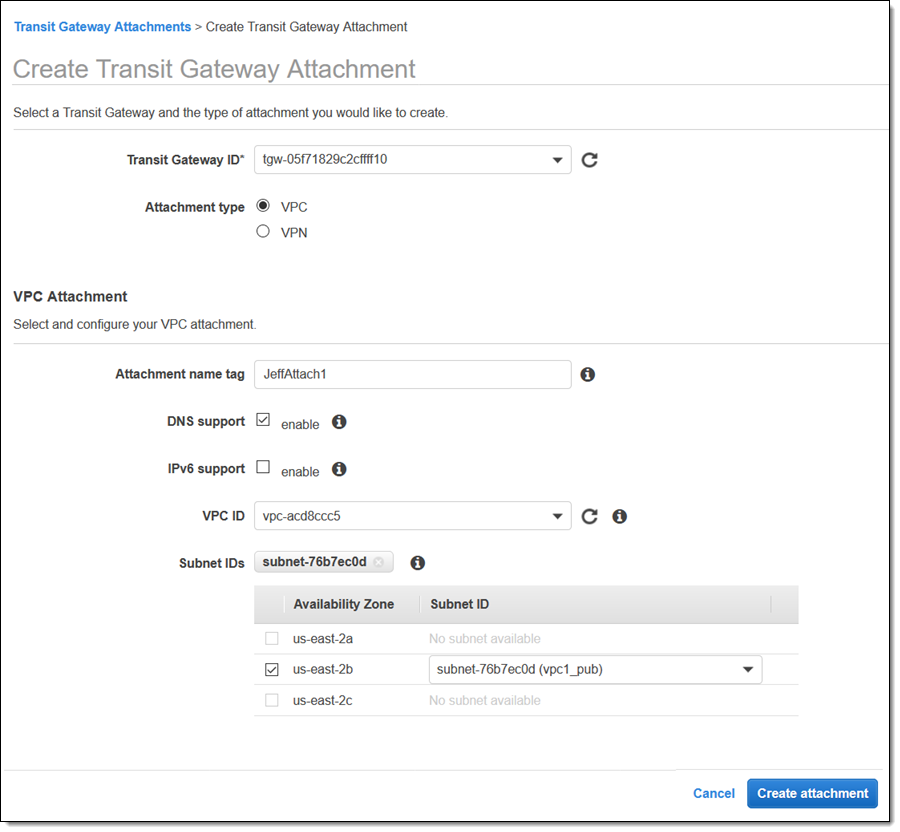
After that, I head over to the Resource Access Manager Console and click Create a resource share:
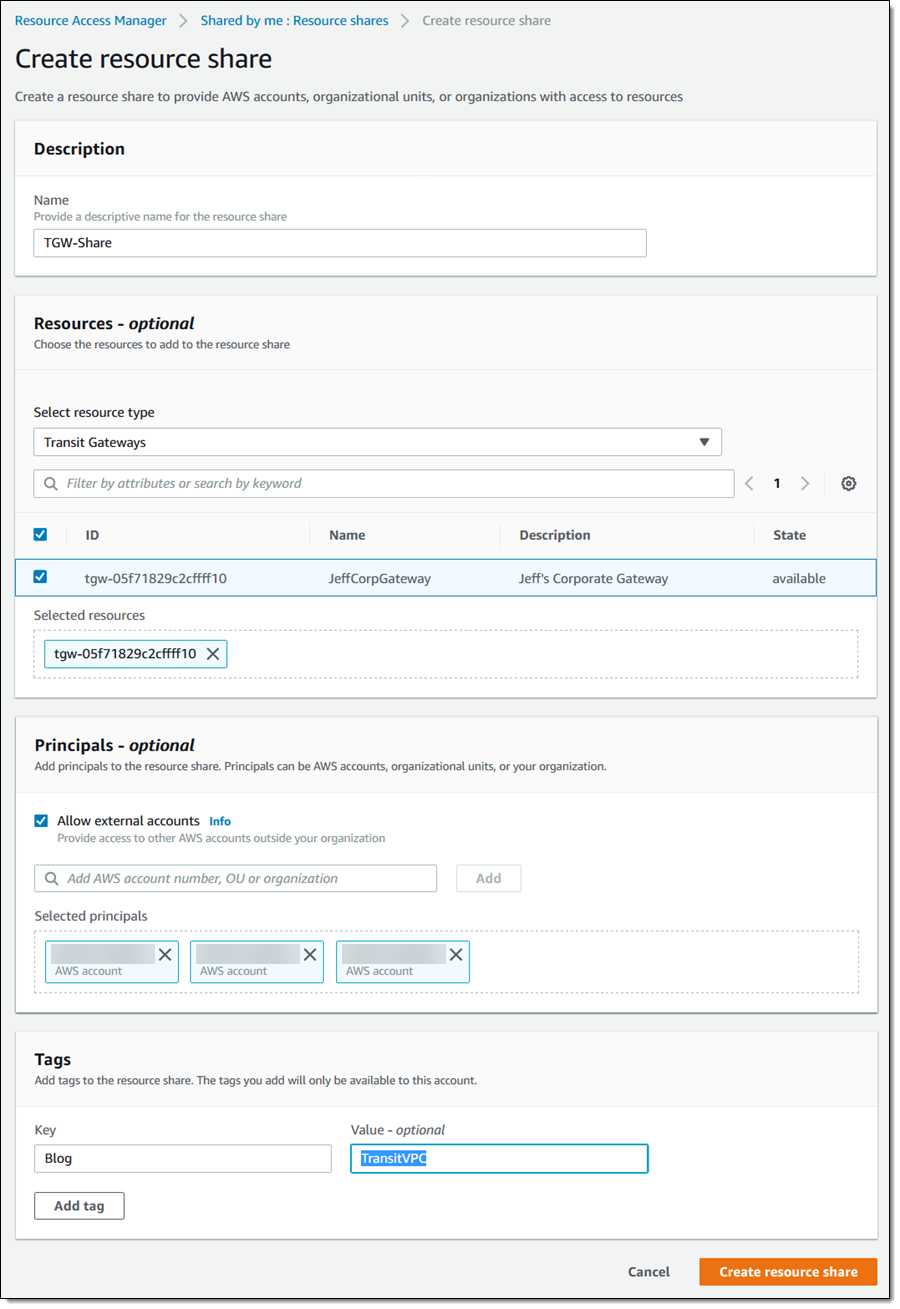
I name my share, find and add my Transit Gateway to it, and add the AWS accounts that I want to share it with. I can also choose to share it with an Organization or an Organizational Unit (OU). I make my choices and click Create resource share to proceed:
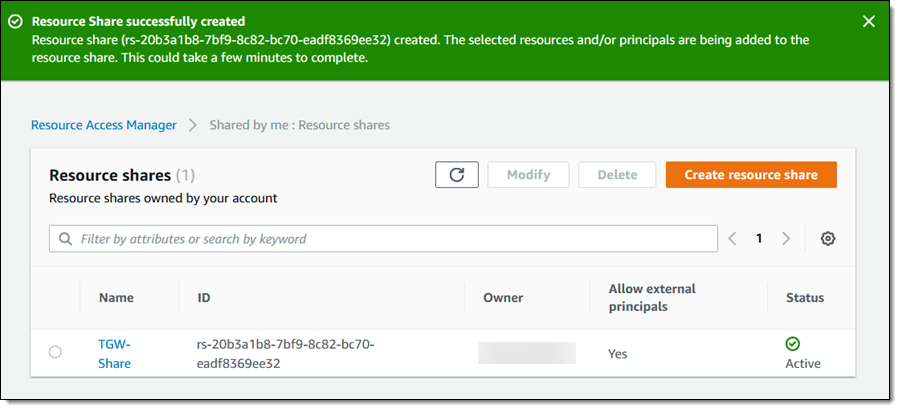
My resource share is created and ready to go within a few minutes:
Next, I log in to the accounts that I shared the gateway with, head back to the RAM Console, locate the invitation, and click it:
I confirm that I am accepting the desired invitation, and click Accept resource share:
I confirm my intent, and then I can see the Transit Gateway as a resource that is shared with me:
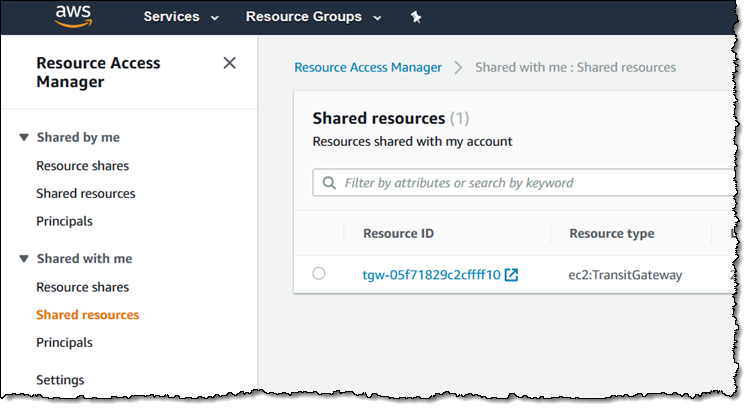
The next step (not shown) is to attach it to the desired VPCs in this account!
As you can see, you can use Transit Gateways to simplify your networking model. You can easily build applications that span multiple VPCs and you can share network services across them without having to manage a complex network. For example, you can go from this:
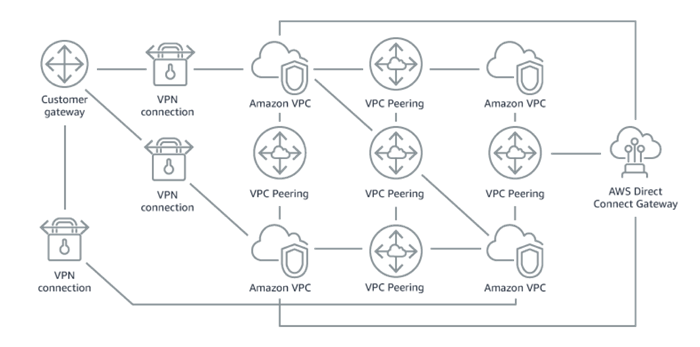
To this:
You can also connect a Transit Gateway to a firewall or an IPS (Intrusiong Prevention System) and create a single VPC that handles all ingress and egress traffic for your network.
Things to Know
Here are a couple of other things that you should know about VPC Transit Gateways:
AWS Integration – The Transit Gateways publish metrics to Amazon CloudWatch and also generate VPC Flow Logs records.
VPN ECMP Support -You can enable Equal-Cost Multi-Path (ECMP) support on your VPN connections. If the connections advertise the same CIDR blocks, traffic will be distributed equally across them.
Routing Domains – You can use multiple route tables on the same Transit Gateway and use them to control routing on a per-attachment basis. You can isolate VPC traffic or divert traffic from certain VPCs to a separate inspection domain.
Security – You can use VPC security groups and network ACLs to control the flow of traffic between your on-premises networks.
Pricing – You pay a per-hour fee for each hour that a Transit Gateway is attached, along with a per-GB data processing fee.
Direct Connect – We are working on support for AWS Direct Connect.
Regions – AWS Transit Gateway is available in US East (N. Virginia),US East (Ohio), US West (Oregon), US West (N. California), Europe (Ireland), and Asia Pacific (Mumbai) AWS Regions. Support for other AWS Regions is coming soon.
Available Now
AWS Transit Gateways are available now and you can start using them today!
— Jeff;
Source: AWS News


