New – Use Tag Policies to Manage Tags Across Multiple AWS Accounts
 Shortly after we launched EC2, customers started asking for ways to identify, classify, or categorize their instances. We launched tagging for EC2 instances and other EC2 resources way back in 2010, and have added support for many other resource types over the years. We added the ability to tag instances and EBS volumes at creation time a few years ago, and also launched tagging APIs and a Tag Editor. Today, tags serve many important purposes. They can be used to identify resources for cost allocation, and to control access to AWS resources (either directly or via tags on IAM users & roles). In addition to these tools, we have also provided you with comprehensive recommendations on Tag Strategies, which can be used as the basis for the tagging standards that you set up for your own organization.
Shortly after we launched EC2, customers started asking for ways to identify, classify, or categorize their instances. We launched tagging for EC2 instances and other EC2 resources way back in 2010, and have added support for many other resource types over the years. We added the ability to tag instances and EBS volumes at creation time a few years ago, and also launched tagging APIs and a Tag Editor. Today, tags serve many important purposes. They can be used to identify resources for cost allocation, and to control access to AWS resources (either directly or via tags on IAM users & roles). In addition to these tools, we have also provided you with comprehensive recommendations on Tag Strategies, which can be used as the basis for the tagging standards that you set up for your own organization.
Beyond Good Intentions
All of these tools and recommendations create a strong foundation, and you might start to use tags with only the very best of intentions. However, as Jeff Bezos, often reminds us, “Good intentions don’t work, but mechanisms do.” Standardizing on names, values, capitalization, and punctuation is a great idea, but challenging to put in to practice. When tags are used to control access to resources or to divvy up bills, small errors can create big problems!
Today we are giving you a mechanism that will help you to implement a consistent, high-quality tagging discipline that spans multiple AWS accounts and Organizational Units (OUs) within an AWS Organization. You can now create and apply Tag Policies and apply them to any desired AWS accounts or OUs within your Organization, or to the the entire Organization. The policies at each level are aggregated into an effective policy for an account.
Each tag policy contains a set of tag rules. Each rule maps a tag key to the allowable values for the key. The tag policies are checked when you perform operations that affect the tags on an existing resource. After you set up your tag policies, you can easily discover tagged resources that do not conform.
Creating Tag Policies
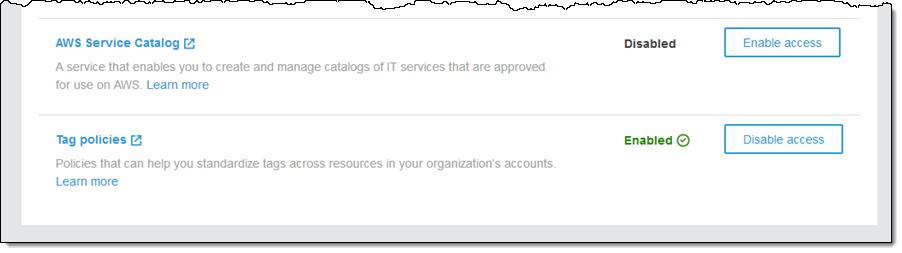
Tag Policies are easy to use. I start by logging in to the AWS account that represents my Organization, and ensure that it has Tag policies enabled in the Settings:
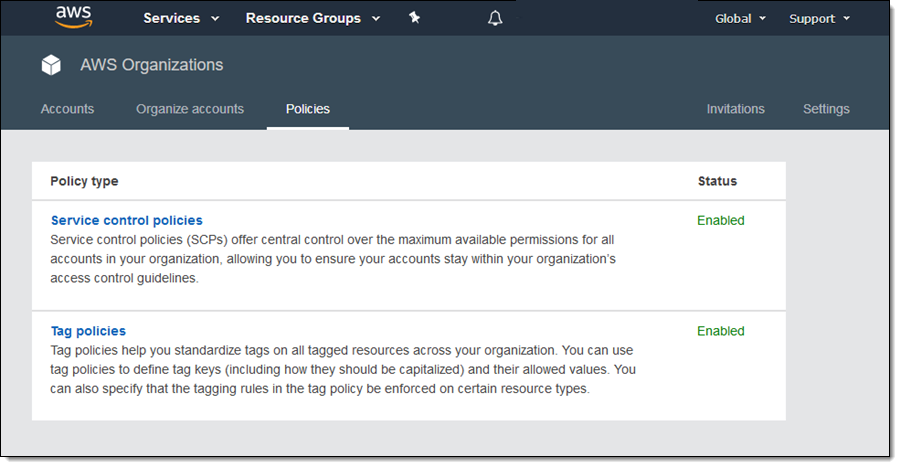
Then I click Policies and Tag policies to create a tag policy for my Organization:
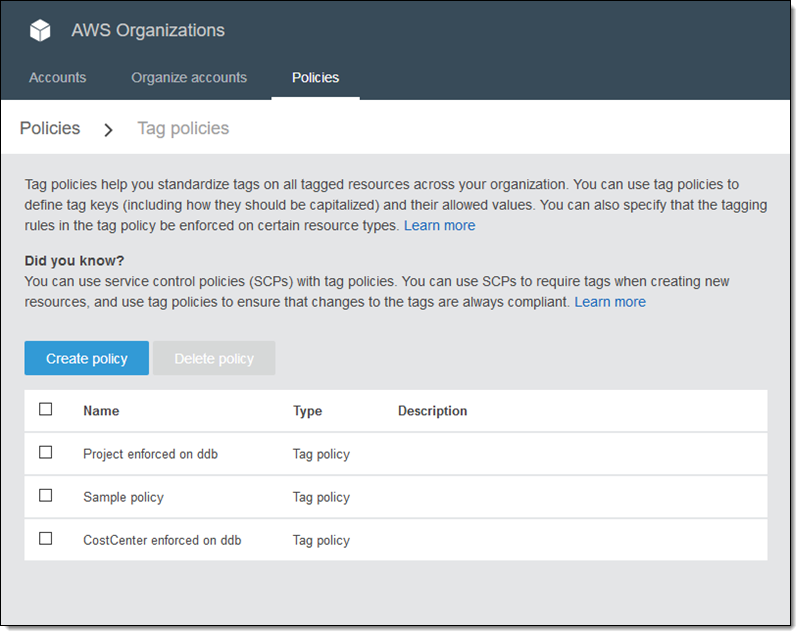
I can see my existing policies, and I click Create policy to make another one:
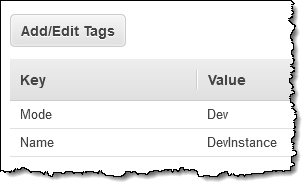
I enter a name and a description for my policy:
Then I specify the tag key, indicate if capitalization must match, and optionally enter a set of allowable values:
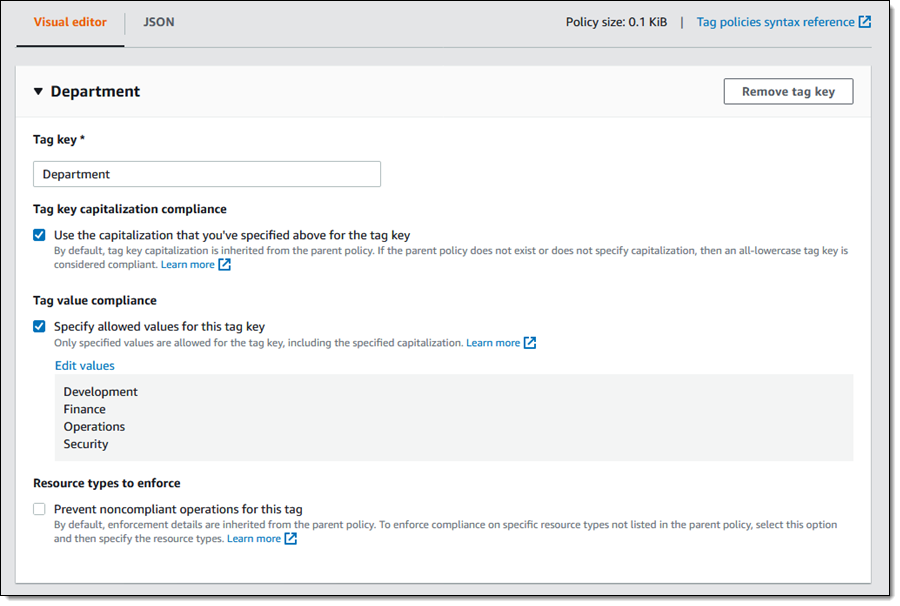
I have three options at this point:
Create Policy – Create a policy that advises me (via a report) of any noncompliant resources in the Root, OUs, and accounts that I designate.
Add Tag Key – Add another tag key to the policy.
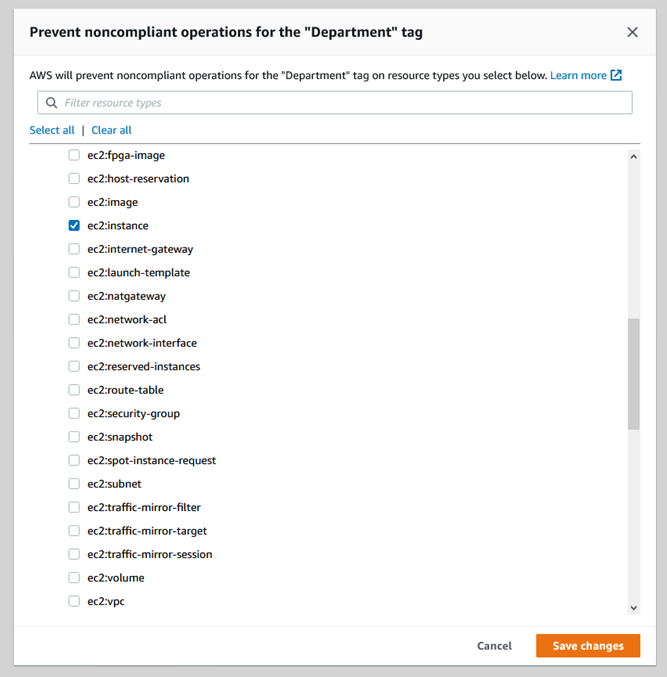
Prevent Noncompliant Operations – Strengthen the policy so that it enforces the proper use of the tag by blocking noncompliant operations. To do this, I must also choose the desired resource types:
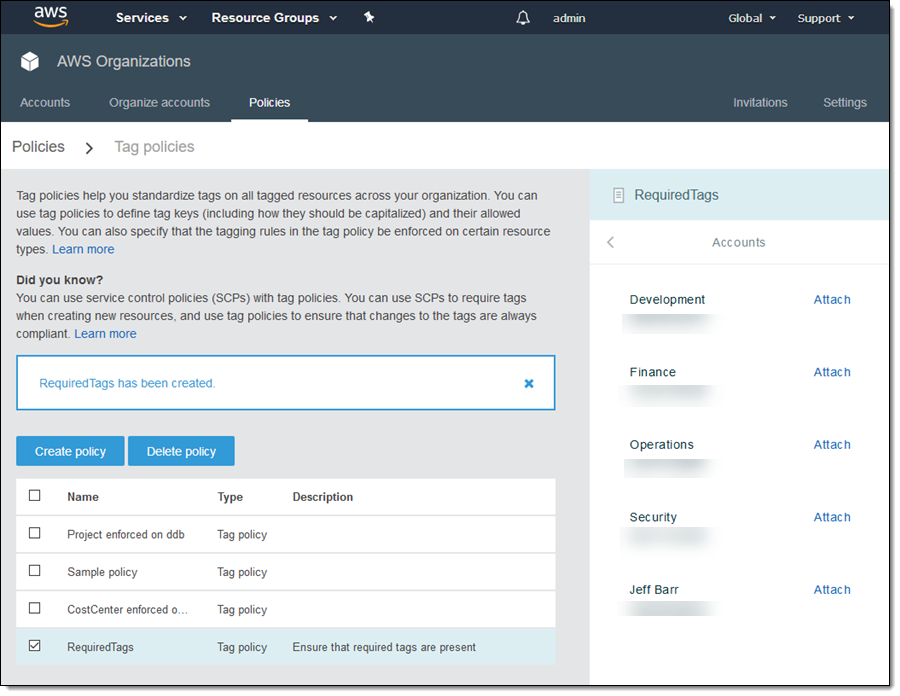
Then I click Create policy, and I am ready to move ahead. I select my policy, and can then attach it to the Root, or to any desired OUs or Accounts:
Checking Policy Compliance
Once I have created and attached a policy, I can visit the Tag policies page in the Resource Groups console to check on compliance:
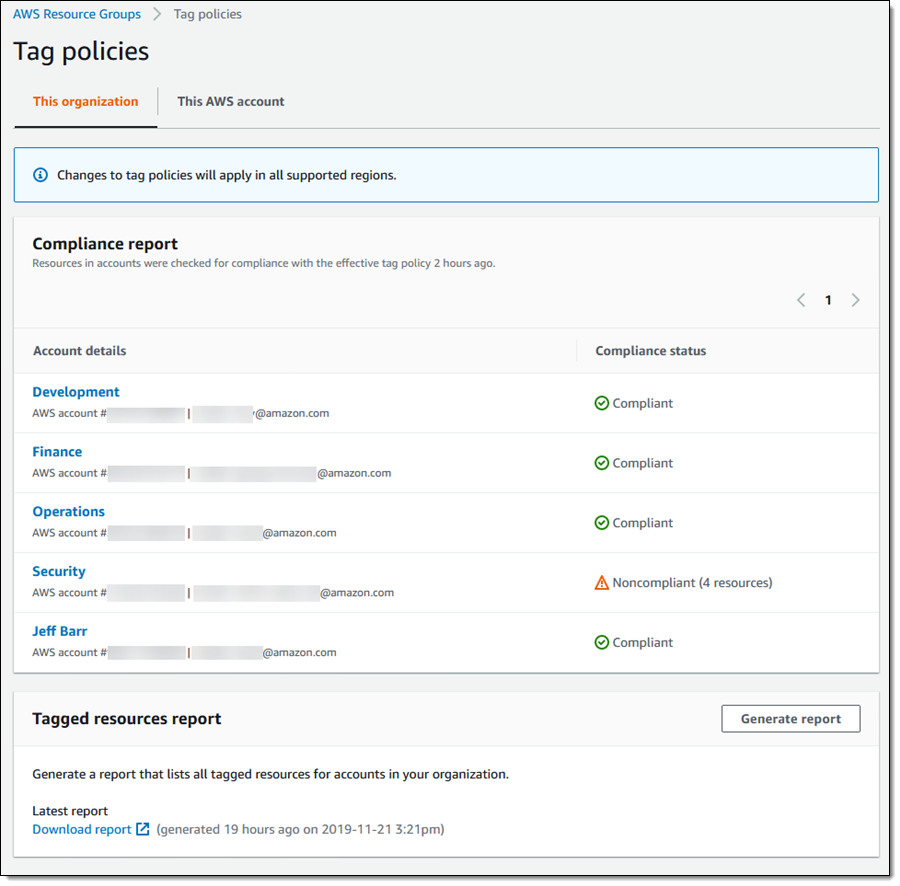
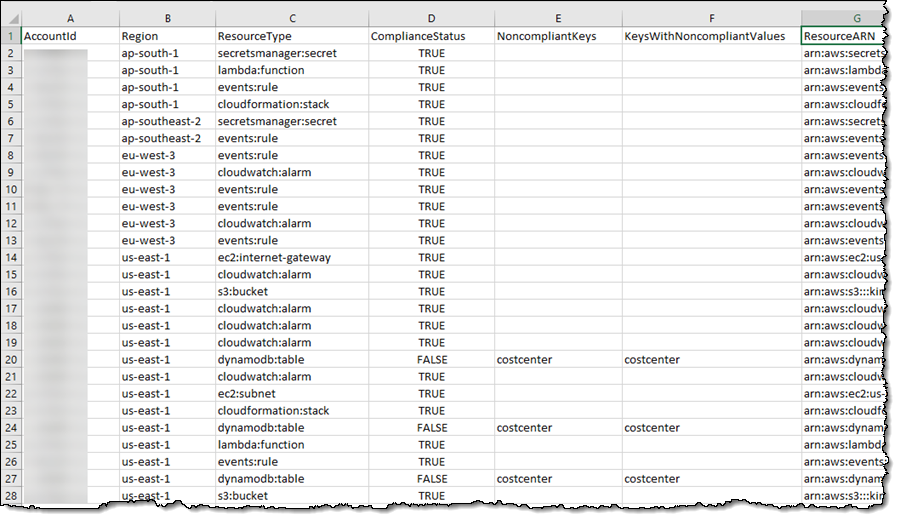
I can also download a compliance report (CSV format), or request that a fresh one be generated:
Things to Know
Here are a couple of things to keep in mind:
Policy Inheritance – The examples above used the built-in inheritance system: Organization to OUs to accounts. I can also fine-tune the inheritance model in order to add or remove acceptable tag values, or to limit the changes that child policies are allowed to make. To learn more, read How Policy Inheritance Works.
Tag Remediation – As an account administrator, I can use the Resource Groups console to view the effective tag policy (after inheritance) so that I can take action to fix any non-compliant tags.
Tags for New Resources – I can use Org-level Service Control Policies or IAM policies to prevent the creation of new resources that are not tagged in accord with my organization’s internal standards (see Require a Tag Upon Resource Creation for an example policy).
Access – This new feature is available from the AWS Management Console, AWS Command Line Interface (CLI), and through the AWS SDKs.
Available Now
You can use Tag Policies today in all commercial AWS Regions, at no extra charge.
— Jeff;
Source: AWS News


